#
Infrastructure for ATT&CK Evaluations - ALPHV BlackCat and menuPass (2024)
The infrastructure below was used for both ALPHV BlackCat and menuPass (2024). For convenience and cost savings, shared resources are used, including supporting infrastructure, including attacker platform, DNS, mail server, and traffic forwarding hosts.
Initial infrastructure was setup using Terraform, with configuration applied via scripts and configuration files.
Infrastructure for ATT&CK Evaluations - ALPHV BlackCat and menuPass (2024) Infrastructure Overview Scenario VMs Subsidiary A Domain - digirunaway.net Subsidiary B Domain - digirevenge.net Standalone Workstation
Support and Red Team Hosts Network Support Hosts Red Team Hosts
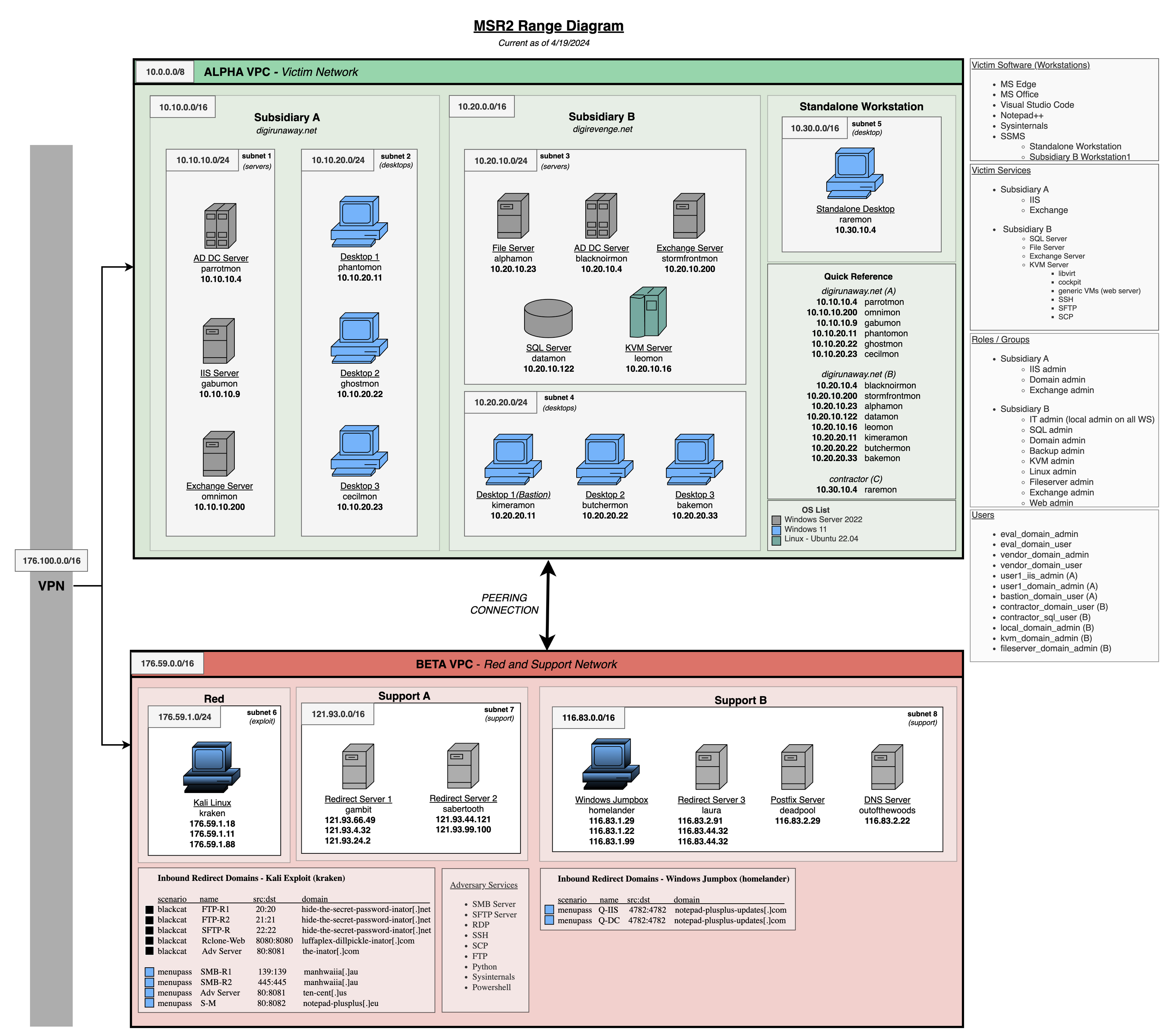
Network Diagram
#
Infrastructure Overview
This document provides an overview of the infrastructure support used for the evaluation. In addition to setup and configuration of virtual machines, this document covers infrastructure support services, such as domain name services (DNS), mail, and traffic redirection, used to support the evaluation. Support services such as DNS and redirectors are used throughout the evaluation for resource efficiency.
The Digimon media franchise was used as inspiration for the naming scheme.
#
Scenario VMs
The scenario consists of an organization with two subsidiaries, with a bidirectional Active Directory domain trust relationship between the domains. A separate workstation, outside of the two domains, represents a 3rd party user with trusted access to the domain systems.
#
Subsidiary A Domain - digirunaway.net
The Subsidiary A domain consists of six virtual machines, all joined to the digirunaway.net Windows domain.
#
Subsidiary B Domain - digirevenge.net
The Subsidiary B domain consists of eight virtual machines, all joined to the digirevenge.net Windows domain.
#
Standalone Workstation
The Standalone Workstation is a single virtual machine, not joined to an Active Directory domain.
#
Support and Red Team Hosts
The following hosts are used for overall network support, as well as for red team use. The hosts below are not accessible by evaluation participants.
#
Network Support Hosts
#
Red Team Hosts
#
Network Diagram
The diagram below shows the layout of all victim hosts, attack platform, and support hosts.